What you need to know about managerial roles within cybersecurity
When it comes to protecting digital assets, managerial roles are just as crucial as technical ones. These roles range from policy development to compliance, and from managing security awareness programs to ensuring that security practices align with business objectives.
While these roles may not involve coding or hands-on testing, they require a deep understanding of cybersecurity principles, effective communication skills, and a strategic mindset. For those entering the cybersecurity field in a managerial capacity, the CompTIA Security+ certification is an excellent entry-level option. It provides a foundational understanding of cybersecurity concepts, blending basic technical knowledge with essential security principles. After completing this certification, professionals in managerial positions will be better equipped to understand the technical aspects of cybersecurity and collaborate effectively with technical teams.
Here’s a look at some managerial roles in cybersecurity and the essential skills needed to pursue them.
Managerial cybersecurity career pathways and certifications
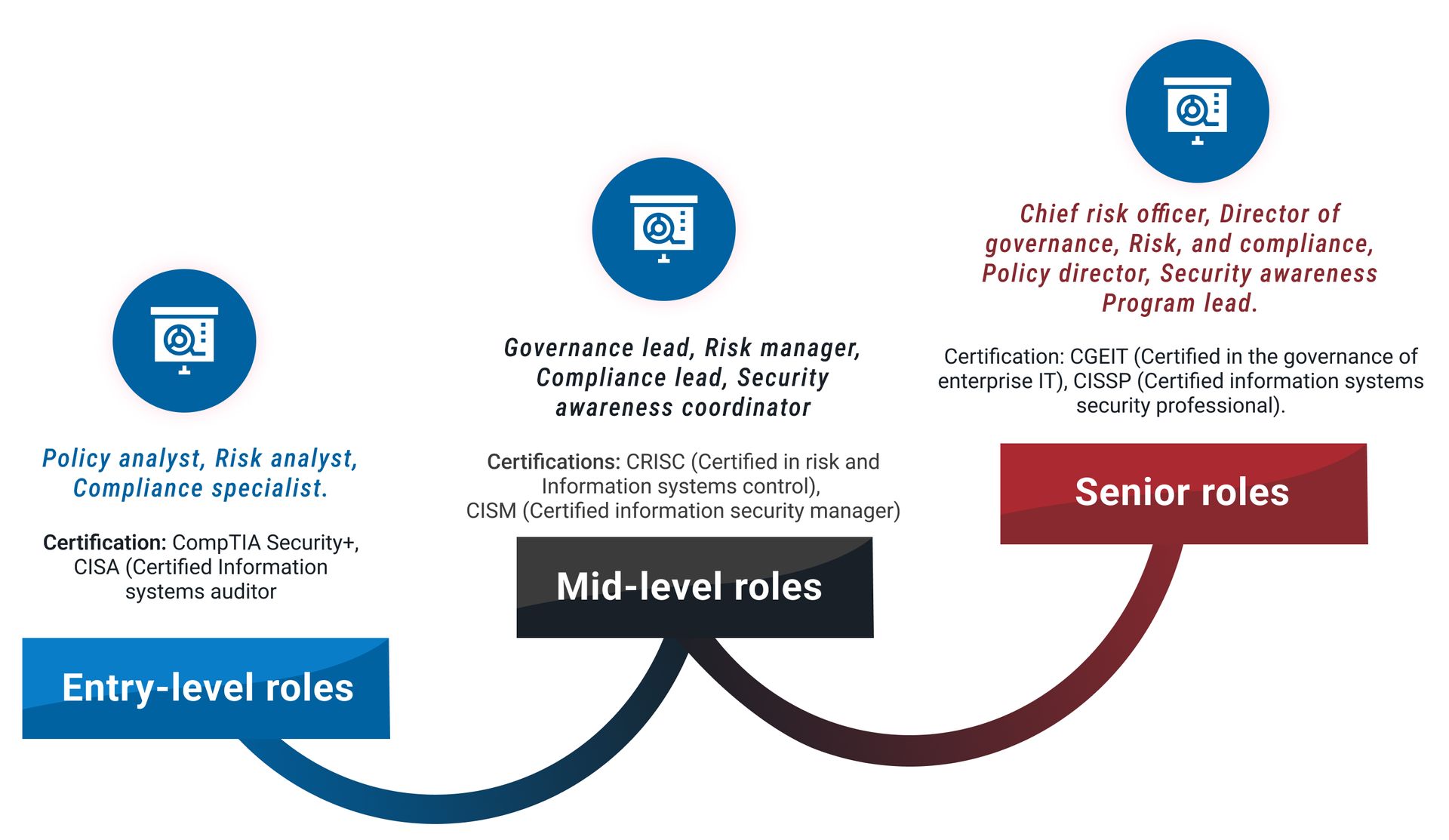
This graphic will help visualize the typical career pathways for non-technical roles in cybersecurity, showing progression and relevant certifications for each stage.
Cybersecurity policy and governance
Policy development and enforcement
One of the foundational aspects of a robust cybersecurity framework is having well-defined policies and governance structures. Cybersecurity policy and governance professionals are responsible for developing, implementing, and enforcing policies that ensure the security of an organization's digital assets. These policies may cover everything from data protection and access controls to incident response and user behavior guidelines.
To succeed in this role, you need a strong understanding of regulatory requirements and industry standards such as GDPR, HIPAA, and ISO/IEC 27001. Equally important is the ability to work closely with various departments to ensure that policies are practical and enforceable. This requires excellent communication skills, as you will need to translate complex security concepts into policies that non-technical staff can understand and follow.
Risk management and compliance
Risk management is a critical area within cybersecurity governance. Professionals in this role assess the organization’s risk posture, identify potential threats, and develop strategies to mitigate these risks. They work closely with technical teams to ensure that all potential vulnerabilities are addressed and that the organization complies with relevant regulations and standards.
A successful career in risk management and compliance requires a deep understanding of both cybersecurity principles and business operations. You need to be able to evaluate the impact of security risks on the organization’s objectives and prioritize them accordingly. Strong analytical skills are essential, as is the ability to communicate risks and compliance requirements to senior management and other stakeholders.
Security awareness and training
Developing security awareness programs
Security awareness professionals are responsible for developing and implementing training programs that educate staff on best practices within cybersecurity. This includes everything from recognizing phishing emails to understanding the importance of strong passwords and the proper handling of sensitive information.
To excel in this role, you need to be a skilled educator and communicator. You must be able to create engaging training materials that resonate with employees at all levels of the organization. An understanding of human behavior will also be an important asset, as you will need to design programs that not only inform but also motivate employees to adopt secure practices in their daily work.
Behavioral analysis and insider threat management
Beyond general security awareness, some professionals focus specifically on understanding and managing insider threats. Insider threat management involves identifying and mitigating risks that come from within the organization, such as employees or contractors who may intentionally or unintentionally cause harm. This role requires a keen understanding of human behavior and the ability to analyze patterns that might indicate potential insider threats.
Professionals in this field often work closely with human resources and legal departments to develop policies and procedures that detect and address insider threats. A background in psychology or behavioral science can be particularly beneficial, as can experience in conducting investigations and handling sensitive information.
Cybersecurity project management
Managing security projects
In any organization, implementing new security measures or responding to security incidents often involves complex projects that need to be carefully managed. Cybersecurity project managers are responsible for planning, executing, and overseeing these projects, ensuring that they are completed on time, within scope, and on budget.
This role requires strong organizational skills and the ability to coordinate efforts across different teams, including IT, legal, and business units. A deep understanding of cybersecurity concepts is necessary to effectively manage these projects, but equally important is the ability to communicate project goals, progress, and challenges to both technical and non-technical stakeholders.
Change management
Cybersecurity often involves changes to systems, processes, or behaviors that can be disruptive to an organization. Change management professionals work to ensure that these changes are implemented smoothly and with minimal resistance. This involves preparing and supporting the organization through the change process, addressing any concerns, and ensuring that the benefits of the changes are realized.
To be effective in change management, you need strong interpersonal skills and the ability to lead and inspire others. Understanding the organization's culture and how people are likely to react to change is crucial. This role often requires working closely with communication teams to craft messages that help ease the transition and reduce any potential friction.
Vendor management and third-party risk
Evaluating and managing vendor relationships
In today’s interconnected world, organizations often rely on third-party vendors to provide various services, including cloud storage, IT support, and software development. However, these relationships can introduce additional security risks. Vendor management professionals are responsible for assessing the security practices of third-party vendors, ensuring they meet the organization’s security requirements, and managing the ongoing relationship to mitigate risks.
This role requires a strong understanding of both cybersecurity and business practices. You need to be able to evaluate vendors' security measures and negotiate contracts that include appropriate security provisions. Effective communication and negotiation skills are essential, as is the ability to manage relationships with vendors over the long term.
Third-party risk assessment
Closely related to vendor management is the role of third-party risk assessment. Professionals in this area focus on identifying and mitigating risks associated with third-party relationships. This involves conducting regular assessments of vendors’ security practices, monitoring their compliance with security standards, and ensuring that any risks are promptly addressed.
To excel in this role, you need strong analytical skills and a deep understanding of cybersecurity principles. The ability to work with legal and compliance teams is also important, as you will need to ensure that third-party relationships comply with regulatory requirements and do not expose the organization to undue risk.
Ethics and legal knowledge in cybersecurity management
In cybersecurity management, understanding and applying ethical standards and legal regulations are critical. Ethics guide decision-making, particularly when balancing privacy concerns with security needs. Core principles like transparency, accountability, and responsible data handling are essential in building trust with stakeholders, especially in cases of data breaches where openness is crucial. Upholding these ethical principles also ensures that an organization’s data protection practices respect user privacy and build a culture of accountability.
Equally important is navigating complex legal frameworks, including data privacy laws like GDPR, HIPAA, and CCPA. Managers must ensure compliance with these regulations to prevent penalties and protect the organization’s reputation. Key legal responsibilities include securing personal data, adhering to incident reporting protocols, and ensuring third-party compliance with security standards. Certifications such as Certified Information Privacy Manager (CIPM) and Certified Information Security Manager (CISM) can deepen a manager’s knowledge of legal compliance and ethical best practices, positioning them to make informed, responsible decisions.
Final thoughts
While technical skills are often highlighted in cybersecurity, non-technical roles are equally vital to the overall security posture of an organization. These roles require a blend of strategic thinking, communication skills, and a deep understanding of both cybersecurity principles and business operations. By mastering these skills, you can build a successful career in cybersecurity, playing a key role in protecting digital environments from threats and ensuring that security practices align with organizational goals.
Share this article











