What you need to know about becoming a penetration tester in 2024
In Cybersecurity, penetration testers, also known as Certified Ethical Hackers (CEH), play a crucial role in protecting digital assets. These professionals simulate cyberattacks to identify and address vulnerabilities before malicious hackers can exploit them. By thinking like attackers, they help organizations strengthen their defenses and safeguard sensitive information.
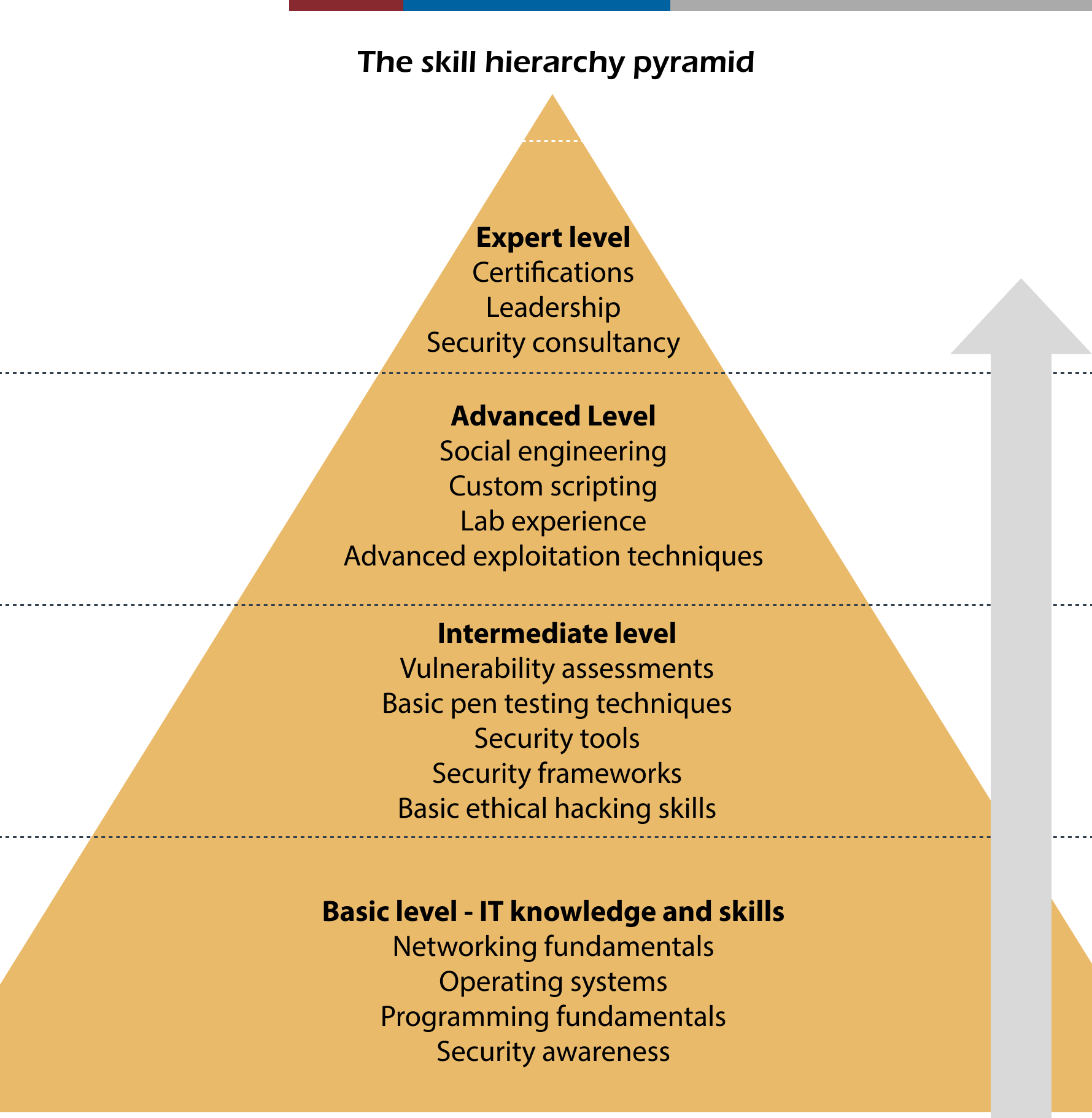
But what does it take to become a successful penetration tester? Let's explore the key skills needed to excel in this highly sought-after role.
Understanding networking
To succeed as a penetration tester, a strong understanding of networking is essential. Networking forms the foundation of any IT system, and as a penetration tester, you need to know how data moves through networks, the protocols involved, and where potential vulnerabilities might exist.
Key protocols like TCP/IP, DNS, and HTTP/HTTPS are particularly important because they are fundamental to how data is transmitted and accessed online. For example, understanding how TCP/IP governs data flow across networks can help you spot weaknesses in packet management. Similarly, knowing how DNS translates domain names into IP addresses is crucial, as vulnerabilities here can lead to significant security issues, such as DNS spoofing attacks.
Beyond just knowing these protocols, you also need to understand how different network components—such as routers, switches, and firewalls—interact and how their configurations can either protect or expose potential weaknesses. This comprehensive understanding of networking enables penetration testers to identify entry points and assess the broader impact of security flaws.
Operating systems proficiency
A key area of expertise for penetration testers is a deep knowledge of operating systems, particularly Linux and Windows. Proficiency in multiple operating systems is crucial because each environment has its own unique set of characteristics and vulnerabilities.
Linux, often dubbed the "hacker's playground," is particularly important because many penetration testing tools are designed to run on Linux distributions like Kali Linux. This system offers a flexible, open-source environment that's ideal for security testing, making it a staple in a penetration tester's toolkit. For example, tools like Metasploit and Nmap, which we'll discuss later, are often used in Linux environments.
Equally critical is understanding Windows environments. Given that many corporate networks rely heavily on Microsoft technology, being familiar with Windows' architecture, permissions, and security protocols is essential. For instance, knowing how to navigate and exploit Windows Active Directory can be crucial in many penetration testing scenarios.
Each operating system presents its own challenges and potential vulnerabilities. A skilled penetration tester needs to navigate both environments effectively to uncover and address security flaws, adapting their approach based on the target system.
Programming and scripting skills
While not strictly mandatory, programming and scripting skills greatly enhance a penetration tester's ability to perform their job effectively. Understanding languages like Python, Bash, PowerShell, and JavaScript can make a significant difference in your capabilities.
These languages are widely used in cybersecurity for various purposes:
- Python:
Known for its versatility, Python is often used for scripting and automation in security tasks. For example, you might use Python to create custom tools for data analysis or to automate repetitive testing processes.
- Bash: Powerful for managing system commands on Linux, Bash scripting can help you quickly perform complex system operations or automate routine tasks.
- PowerShell:
Similar to Bash but for Windows environments, PowerShell is essential for managing and automating Windows systems during penetration tests.
- JavaScript: Essential for web-related testing, particularly when dealing with vulnerabilities in web applications. Understanding JavaScript can help you identify and exploit client-side vulnerabilities.
By perfecting these programming skills, a penetration tester can not only identify vulnerabilities more efficiently, but also create customized solutions tailored to specific scenarios. This adaptability is crucial in the ever-evolving landscape of cybersecurity threats.
Web application security
As web-based services continue to grow, web application security has become a central focus in cybersecurity. Penetration testers need to be well-versed in identifying and exploiting vulnerabilities within web applications.
Common vulnerabilities include:
- SQL injection: Attackers can manipulate a database via a web application's input fields. For example, an attacker might input malicious SQL code into a login form to bypass authentication.
- Cross-site scripting (XSS):
This allows attackers to inject malicious scripts into web pages viewed by other users. A successful XSS attack could lead to session hijacking or defacement of the website.
- Cross-site request forgery (CSRF): In this attack, unauthorized commands are transmitted from a user that the web application trusts. For instance, an attacker might trick a user into clicking a link that performs an unwanted action on a trusted site.
Tools like Burp Suite and OWASP ZAP are invaluable in this domain:
- Burp Suite: A comprehensive platform for performing security testing of web applications, offering features such as scanning, crawling, and manipulating web traffic.
- OWASP ZAP (Zed Attack Proxy): An open-source tool that helps find security vulnerabilities in web applications during the development and testing phases.
Proficiency in these tools allows penetration testers to effectively assess the security posture of web applications and recommend appropriate countermeasures. For example, you might use Burp Suite to intercept and modify requests between a browser and a web application, revealing potential vulnerabilities in the application's input handling.
Specialized tools mastery
Penetration testers rely heavily on a suite of specialized tools to carry out their work. Mastering these tools is a core competency in this field. Some essential tools include:

Being proficient in these tools is vital for any penetration tester, as they form the basis of most testing methodologies and allow for a comprehensive assessment of security risks. Mastery of these tools enables penetration testers to effectively identify, exploit, and document vulnerabilities, providing a robust defense against potential cyber threats.
Certifications
Earning certifications is an effective way to demonstrate and validate your skills as a penetration tester. Some of the most recognized certifications include:
- Certified Ethical Hacker (CEH): Offered by EC-Council, this certification provides a comprehensive overview of various topics including network security and web application testing. It's an excellent starting point for those looking to establish a broad foundation in ethical hacking principles.
- PECB Lead Pen Test Professional: This expert-led penetration testing training course equips professionals with hands-on expertise and cutting-edge knowledge in infrastructure, web application, mobile, and social engineering security. Focusing on practical application, the course develops technical and management skills to lead effective penetration tests, addressing business risks and key issues. Through comprehensive hands-on exercises, simulations, and a final capture-the-flag challenge, participants gain the balanced competencies needed to become respected and professional penetration testers, enhancing their skills and reputation in the field.
- Offensive Security Certified Professional (OSCP): Known for its hands-on, practical approach, the OSCP is highly regarded in the industry. Offered by Offensive Security, it emphasizes real-world penetration testing scenarios, requiring candidates to exploit vulnerabilities in a controlled environment. This certification is particularly respected for its focus on practical skills and the ability to perform under pressure.
- GIAC Penetration Tester (GPEN): Offered by the Global Information Assurance Certification (GIAC), the GPEN dives deeper into the methodologies and technical aspects of penetration testing. It provides a rigorous examination of the processes and techniques used by professionals in the field.
These certifications not only boost your credibility as a penetration tester but also ensure that you stay up to date with the latest tools and techniques in the rapidly evolving cybersecurity landscape. Many employers look for these certifications when hiring, making them valuable assets in your career progression.
Final thoughts
Becoming a successful penetration tester involves a blend of technical knowledge, hands-on experience, and ongoing education. The field of cybersecurity is constantly evolving, with new threats and technologies emerging regularly. As such, a commitment to continuous learning is essential.
By developing a strong foundation in networking, operating systems, and programming, and coupling this with expertise in specialized tools and web application security, you'll be well-equipped to tackle the challenges of this dynamic field. The addition of industry-recognized certifications further validates your skills and opens doors to exciting career opportunities.
Remember, the goal of a penetration tester is not just to find vulnerabilities, but to help organizations improve their overall security posture. Your work will play a crucial role in safeguarding digital environments and contributing to the broader goal of cybersecurity in an increasingly interconnected world.
As you embark on or continue your journey in this field, stay curious, keep practicing, and never stop learning. The world of cybersecurity is vast and ever-changing, offering endless opportunities for growth and impact.
Share this article











